SteamHide Malware Analysis - II
Welcome back :D,
This post is the continuation of SteamHide malware analysis, here we’ll go through the second stage FinalMalware.exe dropped by Hide binary inside image.exe downloader by decrypting the ICC profile after pulling out image from stream profile images. Let’s get started!!
Initial triage for ‘FinalMalware.exe’
File identification
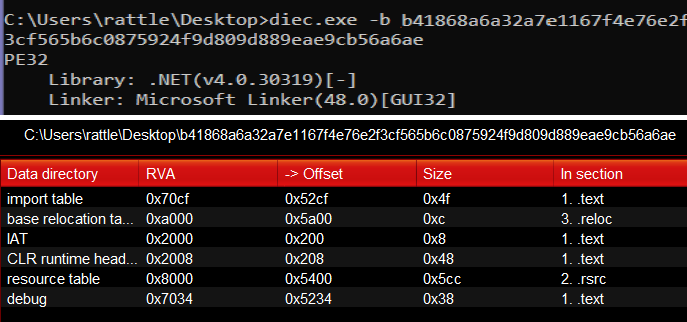 Again
Again DIE and PortexAnalyzer outputs indicates that it’s a PE 32bit .NET managed assembly file, we’ll use dnSpy for further examination
Strings to attach
When a .NET binary is not obfuscated then the strings are good giveaways to its capabilities prior analysis.
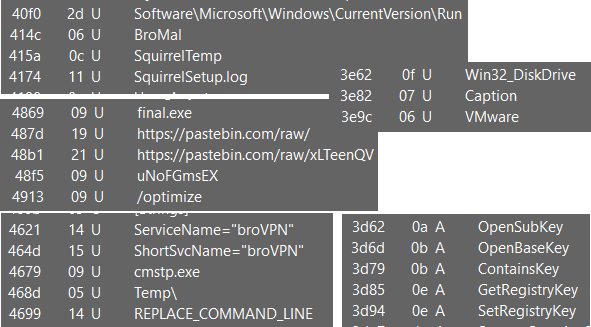
Some interesting strings are follows
- system executable file
cmstp.exe - some registry hives and registry manipulating functions
- functions related to file discovery
- some random but interesting strings like
BroMal,broVPN,uNoFGmsEXand so on - string mentioning
Temp\directory - some pastebin urls
- string mentioning a virtual machine
VMware
How does it behave
Starts with ‘Form1_Load()’
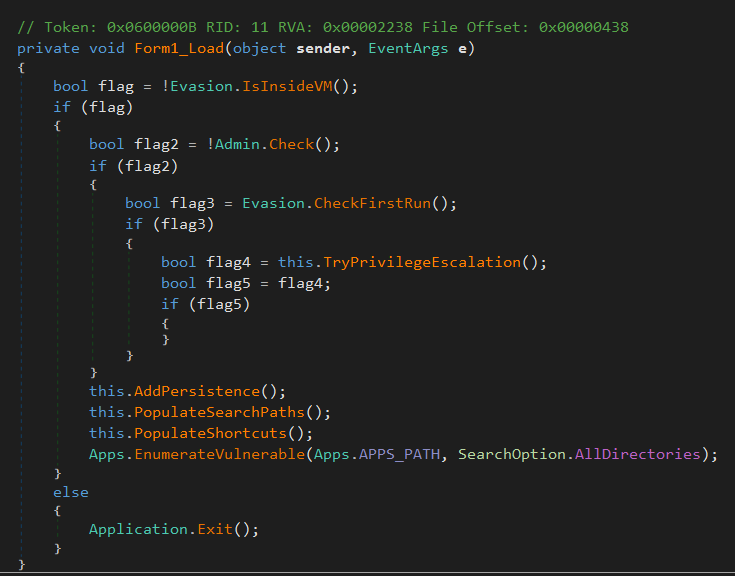
‘Evasion.IsInsideVM()’ : Anti-VM Check
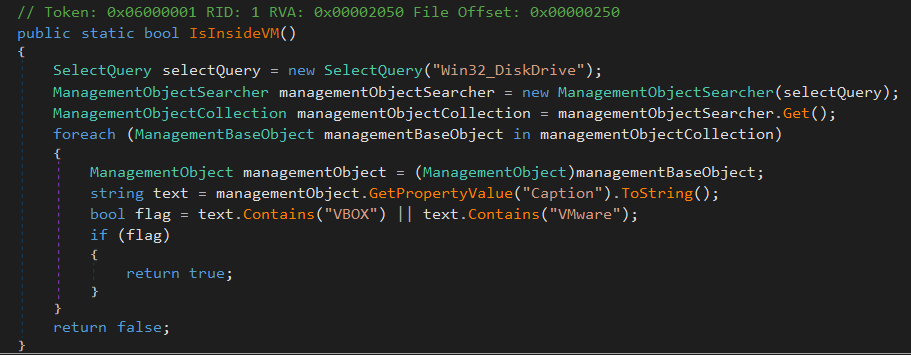
- performs a typical anti-vm technique MITRE ATT&CK T1497.001. This method checks the presence of virtual machine by making a query via
SelectQuery()onWin32_DiskDriveWMI class which represents a physical disk drive of computer running the Windows, - when the ManagementObjectSearcher.Get() method on this object is invoked, the
ManagementObjectSearcherexecutes the given query and returns a collection of management objects(ManagementObjectCollection) that matches the query, then loop through collection to get the value ofWin32_DiskDrive.Captionproperty. But checks for only two VM entries ie.VBOXandVMware, childish enough ‘cause when i debugged this sample in my QEMU based Windows VM, the caption value wasQEMU HARDDISK, resulting in no VM dectection, as you can see below: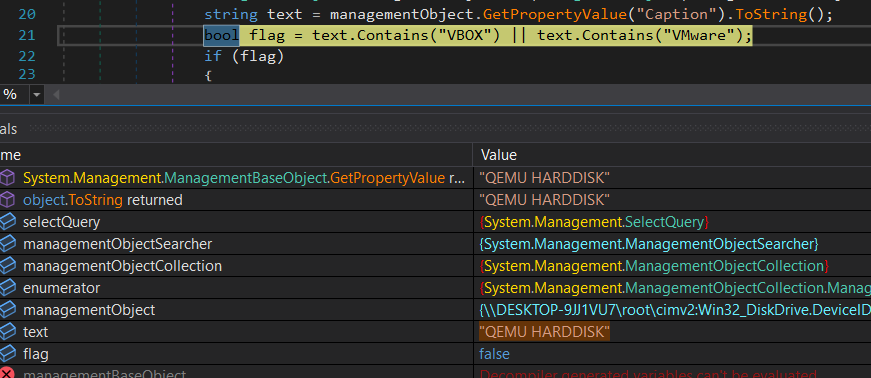
TIP#2: In powershell, run
Get-WmiObject -Class Win32_DiskDriveto check your VM’s caption value
‘Admin.Check()’: are you the admin
On a successful Anti-VM check, it gets the current users WindowsPrincipal(WindowsIdentity.GetCurrent()) windows Identity to check if the user has admin role or not by calling WindowsPrincipal.IsInRole method with WindowsBuiltInRole.Administrator enum which returns a boolean respectively.
‘Evasion.CheckFirstRun()’: am i new here
if user is not admin, checks if the file named ie. uNoFGmsEX\uNoFGmsEX..txt exist under Local Application Data folder of user ie. %LOCALAPPDATA%, if not, then creates one, as shown in Procmon output
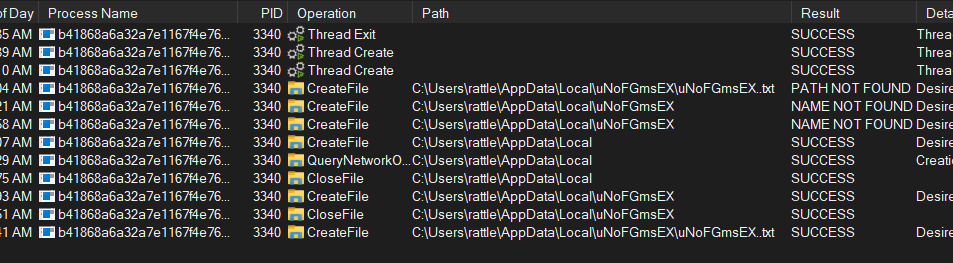
‘Form1.TryPrivilegeEscalation()’: want some power
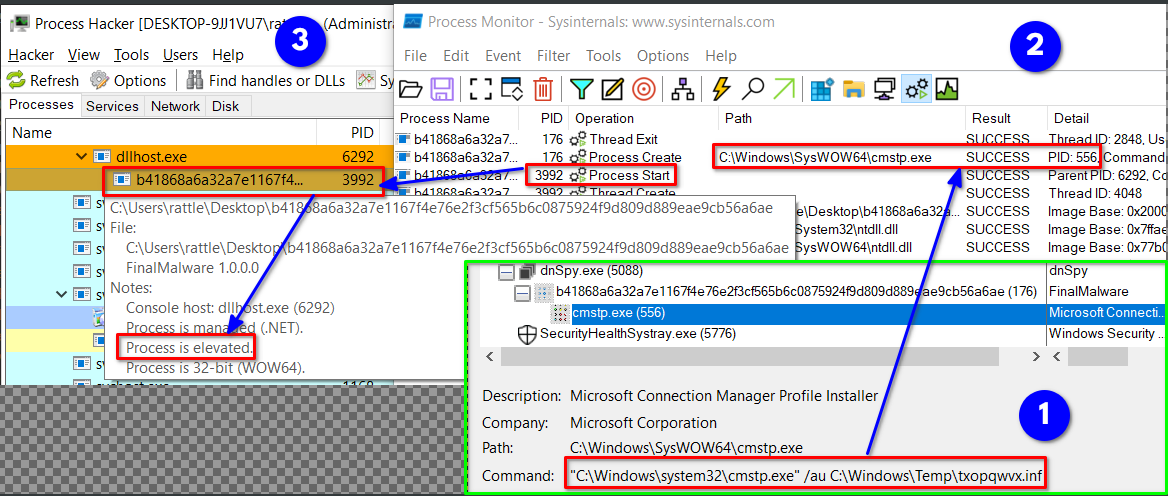
if the sample is running for the first time, then it will try to escalate privileges by utilising the technique MITRE ATT&CK T1218.003 which is performed by exploiting system binary cmstp.exe using the command C:\Windows\system32\cmstp.exe" /au C:\Windows\Temp\[randomFileName].inf which in turn runs the malware with elevated privilege, here’s more on the topic cmstp.exe as lolbin.
See the process in action below
‘Form1.AddPersistence()’: lemme settle for later
- When this sample runs itself with admin privilege via
cmstp.exe, it persist by making auto run key by setting the registry keySoftware\\Microsoft\\Windows\\CurrentVersion\\Run:BroMalwith value set to the malware path itself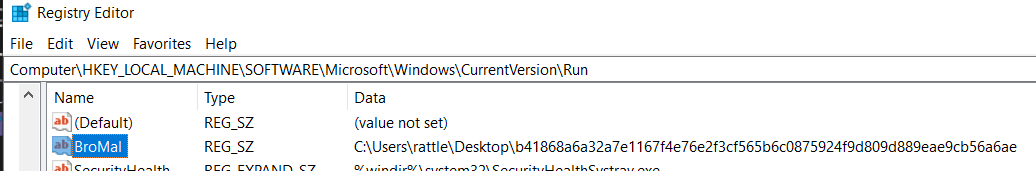
what’s with the shortcuts
PopulateSearchPaths(): stores the paths to userDesktopandDocumentsfolder toShortcutUtils.searchPathsarrayPopulatedShortcuts(): which callsShortcutUtils.EnumerateShortcuts()to traverse through every directory and sub-directories withinsearchPathslooking for the*.lnkfiles, if found then add to theShortcutUtils.shortcutListlist variable- then nothing is done with that at least as of now
‘App.EnumerateVulnerable()’ : your weakness
The malware seems to look for the existence of a SquirrelTemp\SquirrelSetup.log, if found then saves the path, but nothing is done with that info. Maybe to further exploit them
Then the sample abruptly ends.
what does future holds for SteamHide
This version of sample lacks functionality and there’s are many code segments that are either incomplete or not used by now, like:
- there’s a method
CreateTwitterRequestwhich allows making twitter requests, which can be used as twitter bot for C2 and stuff CheckMutexRunning: create a mutex which can be used to avoid re-infecting the systemCodePieceManagerclass : contains method regarding compiling source code to MSIL assembly, maybe to add functionality on the flyUpdaterclass: which can be used to update to a new version in the same way done byhide binary inside image.exedownloader
IOCs
| FinalMalware.exe | b41868a6a32a7e1167f4e76e2f3cf565b6c0875924f9d809d889eae9cb56a6ae |
|---|---|
| AutoRun StartUp Registry Key | BroMal reg key with value being path to malware itself |
| File dropped to check first run | %LOCALAPPDATA%\uNoFGmsEX\uNoFGmsEX..txt |
inf file dropped for cmstp.exe |
C:\Windows\Temp\[randomFileName].inf |
I had fun analyzing this sample and learned a lot in the meantime. Here’s the first hand report by Karsten Hahn Picture this: Malware Hides in Steam Profile Images
Thanks for tuning in, I’ll see you around :)